Application of Hybrid Framework using Gauss Jordan Elimination, Singular Value Decomposition and Linear Binary Pattern Histogram for Image Tampering Recovery
Keywords:
Image tampering detection, Gauss Jordan Elimination, singular value decomposition, local binary pattern histogramAbstract
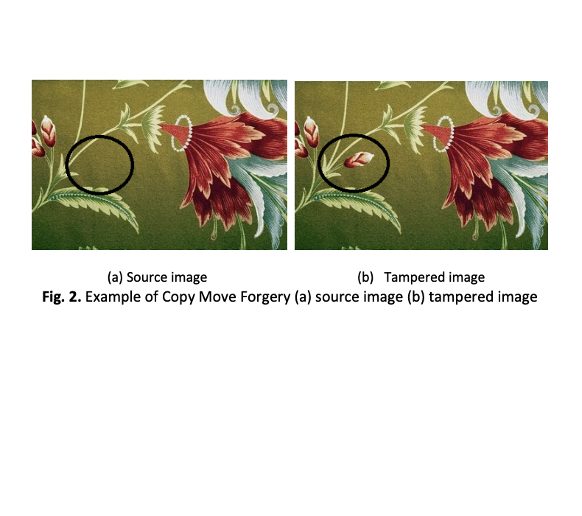
The progress in the last few years in digital editing tools has made image tampering easier. This poses a serious concern in digital forensics, journalism, and law enforcement because manipulated digital content can mislead investigations, spread misinformation, and compromise the integrity of evidence. The research proposes a hybrid framework for image tampering detection and recovery based on Gauss Jordan Elimination (GJE), Singular Value Decomposition (SVD), and Linear Binary Pattern (LBP) Histogram methods. The main goals are to detect the tampered areas accurately, determine the forgery type, which is mainly copy-move and splicing forgery, and recover the original image with minimal distortion. The CASIA 2.0 dataset was used for training and testing. Preprocessing steps included image grayscale conversion and normalization to standardize inputs. Feature extraction involved LBP histogram- based feature extraction while SVD was used for capturing. structural changes and pixel recovery was performed by GJE. The performance of the model was evaluated using PoDA, accuracy, precision, recall, F1-score, memory usage, PSNR, and MSE. On average, results show that the detection of the proposed method gives satisfactory results after copy move forgery as compared with splicing forgery. The research provides a robust and detailed framework for tampering detection and recovery of images in real time and classified images requiring precise and swift digital image verification.